SINGAPORE: They say the air is clearest after the rain.
In the last two weeks, the thunderstorm that is now known as the OCBC SMS scam seems to have cleared with OCBC deciding to absorb its customers’ losses on a goodwill basis and the Monetary Authority of Singapore (MAS) and Association of Banks in Singapore (ABS) announcing measures to boost online security.
Banks now have new responsibilities to proactively tackle such threats by putting in place safeguards like lower thresholds for fund transfers and removing clickable links in emails and SMSes to customers.
With some breathing space, it’s an opportune time to take stock of the situation and decide how organisations must shore up cyber defences so Singapore can continue to move forward as more public transactions and private payments go digital.
We cannot let up this momentum. While the public furore has died down, the perpetrators of this crime are still out there and in possession of their ill-gotten gains. This means that they are now better resourced and even more motivated to try the same trick or come up with a more sinister version.
Undoubtedly, the authorities will pursue the perpetrators and investigations will continue but this is not the first phishing scam and it will not be the last.
We should therefore not waste this teaching opportunity and reflect on how this incident impacts our shared responsibility of cybersecurity. There is no panacea of a magic silver bullet but a variety of issues that we will need to work at.
The MAS/ABS announcement called for more frequent scam education alerts. Like many, I have been receiving scam alerts from various banks and other financial service providers.
For starters, how do I verify these scam alerts? Remember when the SingHealth breach occurred, a fake SMS of unknown origin emerged?
Perhaps it is time for a verified registry of scam alerts, maybe with blockchain technology so that people know the alerts are real.
While this is topical, the real question is how do we create sustainable public education of cybersecurity for the general population? The questions of who should be responsible or best placed for this and when this should be carried out are important questions that should be thought about.
While banks may seem like obvious candidates, many phishing scams have occurred within corporate, personal email and social media systems that include scams masquerading as instructions from a superior using his business email account, pleas for assistance from a social media account and even fake job offers.
We should not just give out fish to make up for phishing losses but educate as many people to identify all manner of phishing scams.
One example is the police advisory on the re-emergence of phishing scams involving emails and text messages. Research has shown that healthcare and education sectors are common cybersecurity targets, which means that even children and the non-banking public need to be cybersecurity-aware.
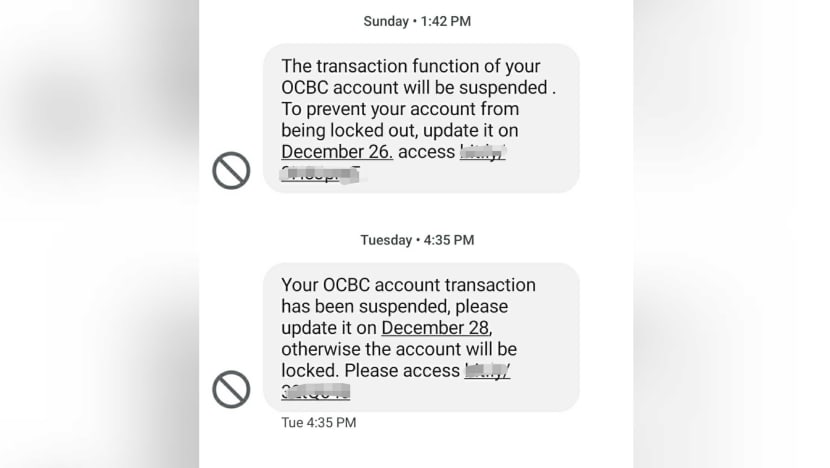
Screengrab of phishing scam messages impersonating OCBC.
In the case of education, many campuses are open and students generally more open to sharing and therefore less careful, making them vulnerable.
Healthcare data may not seem like critical information at first glance but can be valuable data that cause serious issues if they land in the wrong hands.
The measures laid out by MAS/ABS have relevance to the wider industry as a whole, for organisations that have a digital footprint and should be considered by all stakeholders.
It would be a missed opportunity for only banks and financial institutions to take note of these recommendations.
The MAS/ABS measures include having a well-resourced response team to respond to fraud reports and potentially other cybersecurity incidents.
A leaf can be taken out of the Singapore military system, which is familiar to Singaporeans, in particular the National Service (NS) reservist system.
It has a small response team (the equivalent being regulars and NSFs) but is always ready for operations to be scaled up by enlisting the aid of a larger group of experts from other functions (the equivalent being NSmen getting mobilised on recall).
In the event of a major scam or breach, automated responses cannot – and should not – be the default mode. Humans must be part of a response team, tapping on people who have the training and skills to fix the problem quickly.
Both the OCBC and the earlier SingHealth incidents highlighted the need for a quick and sizeable response team that can be readily deployed.
The raft of measures to be undertaken by banks for their Internet banking systems span a range with default thresholds, delay, a cooling-off period and notifications.
These piecemeal measures can help plug temporary gaps so it’s heartening to hear that MAS, the Singapore Police Force and the Infocomm Media Development Authority will be working with banks on more permanent solutions on SMS spoofing, fraud surveillance and immediate recovery systems.
The big picture here is that security is best provided for at the design stage – also known as security by design. Technology is but a partial solution – how you implement the technology matters.
I remember my secondary school Singapore history from many moons ago. We were taught that the guns at Fort Siloso were pointing the wrong way, unable to repel an attack from Peninsular Malaysia.
The technology was not inferior: The guns were good but they were set up wrongly. This was, in effect, a design issue – leading to the weapon being useless when the time of need arrived.

An advisory on the OCBC mobile banking application warning users of fake SMSes containing links to phishing websites.
Similarly, security should be on the forefront when systems and processes are designed and should be regularly reviewed as the landscape changes.
For instance, recognising that the ability to carry out a raft of transactions may not be required by all users nor beneficial to them would then lead designers to differentiate the speed at which certain transactions are executed.
Similarly, the discovery of subsequent vulnerabilities and abnormalities should lead to re-evaluation of design of the system affected by such developments.
The modern CEO will increasingly find that cybersecurity expertise is required at the board level where critical decisions need to be taken in a timely manner.
The MAS Technology Risk Management Guidelines already recommend that a chief information security officer (CISO) position be created as a C-suite level office, alongside the chief technology officer and the chief information officer.
For large organisations, the CISO position is no longer a part-time extension of the CTO or a backroom operation. It is a risk management role with critical decision-making authority.
The CTO and CIO are business functions – ensuring that IT systems are running smoothly, and information is collected and disseminated clearly. The CISO’s main task is to work with them to ensure security considerations form part of the infrastructure design and operations.
This emphasis on cybersecurity is one which non-financial institutions should also emulate. As OCBC CEO Helen Wong remarked this week, responding to a cyberattack is like fighting a war. In the war room, the general will want the commander of a key defensive unit to be there beside him.
Alongside organisational and process changes, regular management training in terms of tabletop and cyber-range training should also be undertaken. This will ensure that teams are prepared and rehearsed for incidents both in theory and in practice.
Again, this is a MAS recommendation that should be considered beyond the financial industry.
It has been argued that those who enjoyed the fruits of digitalisation should share the pain of digitalisation. I don’t propose to go that far but as Spiderman’s uncle Ben put it – those enjoying the great power of digitalisation should accept the great responsibility that come with it.
Bryan Tan is technology and fintech partner at law firm Pinsent Masons and a former Singapore chapter president of the Internet Society. He also teaches at the Chief Information Security Officer Certification programme.
Continue reading...
In the last two weeks, the thunderstorm that is now known as the OCBC SMS scam seems to have cleared with OCBC deciding to absorb its customers’ losses on a goodwill basis and the Monetary Authority of Singapore (MAS) and Association of Banks in Singapore (ABS) announcing measures to boost online security.
Banks now have new responsibilities to proactively tackle such threats by putting in place safeguards like lower thresholds for fund transfers and removing clickable links in emails and SMSes to customers.
With some breathing space, it’s an opportune time to take stock of the situation and decide how organisations must shore up cyber defences so Singapore can continue to move forward as more public transactions and private payments go digital.
We cannot let up this momentum. While the public furore has died down, the perpetrators of this crime are still out there and in possession of their ill-gotten gains. This means that they are now better resourced and even more motivated to try the same trick or come up with a more sinister version.
Undoubtedly, the authorities will pursue the perpetrators and investigations will continue but this is not the first phishing scam and it will not be the last.
We should therefore not waste this teaching opportunity and reflect on how this incident impacts our shared responsibility of cybersecurity. There is no panacea of a magic silver bullet but a variety of issues that we will need to work at.
Related:
CYBERSECURITY PUBLIC EDUCATION
The MAS/ABS announcement called for more frequent scam education alerts. Like many, I have been receiving scam alerts from various banks and other financial service providers.
For starters, how do I verify these scam alerts? Remember when the SingHealth breach occurred, a fake SMS of unknown origin emerged?
Perhaps it is time for a verified registry of scam alerts, maybe with blockchain technology so that people know the alerts are real.
While this is topical, the real question is how do we create sustainable public education of cybersecurity for the general population? The questions of who should be responsible or best placed for this and when this should be carried out are important questions that should be thought about.
While banks may seem like obvious candidates, many phishing scams have occurred within corporate, personal email and social media systems that include scams masquerading as instructions from a superior using his business email account, pleas for assistance from a social media account and even fake job offers.
We should not just give out fish to make up for phishing losses but educate as many people to identify all manner of phishing scams.
One example is the police advisory on the re-emergence of phishing scams involving emails and text messages. Research has shown that healthcare and education sectors are common cybersecurity targets, which means that even children and the non-banking public need to be cybersecurity-aware.

Screengrab of phishing scam messages impersonating OCBC.
In the case of education, many campuses are open and students generally more open to sharing and therefore less careful, making them vulnerable.
Healthcare data may not seem like critical information at first glance but can be valuable data that cause serious issues if they land in the wrong hands.
The measures laid out by MAS/ABS have relevance to the wider industry as a whole, for organisations that have a digital footprint and should be considered by all stakeholders.
It would be a missed opportunity for only banks and financial institutions to take note of these recommendations.
RAPID CYBERSECURITY RESPONSE
The MAS/ABS measures include having a well-resourced response team to respond to fraud reports and potentially other cybersecurity incidents.
A leaf can be taken out of the Singapore military system, which is familiar to Singaporeans, in particular the National Service (NS) reservist system.
It has a small response team (the equivalent being regulars and NSFs) but is always ready for operations to be scaled up by enlisting the aid of a larger group of experts from other functions (the equivalent being NSmen getting mobilised on recall).
Related:
In the event of a major scam or breach, automated responses cannot – and should not – be the default mode. Humans must be part of a response team, tapping on people who have the training and skills to fix the problem quickly.
Both the OCBC and the earlier SingHealth incidents highlighted the need for a quick and sizeable response team that can be readily deployed.
REDESIGNING TECHNOLOGICAL SAFEGUARDS
The raft of measures to be undertaken by banks for their Internet banking systems span a range with default thresholds, delay, a cooling-off period and notifications.
These piecemeal measures can help plug temporary gaps so it’s heartening to hear that MAS, the Singapore Police Force and the Infocomm Media Development Authority will be working with banks on more permanent solutions on SMS spoofing, fraud surveillance and immediate recovery systems.
The big picture here is that security is best provided for at the design stage – also known as security by design. Technology is but a partial solution – how you implement the technology matters.
I remember my secondary school Singapore history from many moons ago. We were taught that the guns at Fort Siloso were pointing the wrong way, unable to repel an attack from Peninsular Malaysia.
The technology was not inferior: The guns were good but they were set up wrongly. This was, in effect, a design issue – leading to the weapon being useless when the time of need arrived.

An advisory on the OCBC mobile banking application warning users of fake SMSes containing links to phishing websites.
Similarly, security should be on the forefront when systems and processes are designed and should be regularly reviewed as the landscape changes.
For instance, recognising that the ability to carry out a raft of transactions may not be required by all users nor beneficial to them would then lead designers to differentiate the speed at which certain transactions are executed.
Similarly, the discovery of subsequent vulnerabilities and abnormalities should lead to re-evaluation of design of the system affected by such developments.
CYBERSECURITY IS A LEADERSHIP PRIORITY
The modern CEO will increasingly find that cybersecurity expertise is required at the board level where critical decisions need to be taken in a timely manner.
The MAS Technology Risk Management Guidelines already recommend that a chief information security officer (CISO) position be created as a C-suite level office, alongside the chief technology officer and the chief information officer.
For large organisations, the CISO position is no longer a part-time extension of the CTO or a backroom operation. It is a risk management role with critical decision-making authority.
The CTO and CIO are business functions – ensuring that IT systems are running smoothly, and information is collected and disseminated clearly. The CISO’s main task is to work with them to ensure security considerations form part of the infrastructure design and operations.
Related:
This emphasis on cybersecurity is one which non-financial institutions should also emulate. As OCBC CEO Helen Wong remarked this week, responding to a cyberattack is like fighting a war. In the war room, the general will want the commander of a key defensive unit to be there beside him.
Alongside organisational and process changes, regular management training in terms of tabletop and cyber-range training should also be undertaken. This will ensure that teams are prepared and rehearsed for incidents both in theory and in practice.
Again, this is a MAS recommendation that should be considered beyond the financial industry.
It has been argued that those who enjoyed the fruits of digitalisation should share the pain of digitalisation. I don’t propose to go that far but as Spiderman’s uncle Ben put it – those enjoying the great power of digitalisation should accept the great responsibility that come with it.
Bryan Tan is technology and fintech partner at law firm Pinsent Masons and a former Singapore chapter president of the Internet Society. He also teaches at the Chief Information Security Officer Certification programme.
Continue reading...